- December 17, 2023
How To Prevent Attacks on iGaming Platforms
Why are many self-built gambling platforms now turning to white label iGaming? With the advent of the Internet era, people around the world have undoubtedly become closer. In this era of information explosion, we can easily transfer information to each other and realize our respective wishes and goals simply through the Internet. However, people's connection to the Internet, whether in life or work, must pay a certain price. Among these, an important area is iGaming platforms. Since it inherently relies on the Internet, all games and transactions in iGaming are conducted over the Internet. This vast Internet world is filled with a group of knowledgeable and skilled people who use various means to bypass network security measures and steal money, data, and other resources. Obviously, the iGaming platform has become an important target of these people's attention. Today, the editor of TC-Gaming will discuss in depth the network security issues of iGaming with all gambling tycoons. Together we will analyze where these cyber threats come from and how to properly prevent them to ensure the security and interests of your gambling platform.
Why attack your betting platform?
In today's digital environment, no business is immune to cyberattacks. Whether it's a small family business or a large international bookmaker, online businesses are vulnerable to hackers. However, large companies not only have financial resources and data resources that can be used or stolen by hackers, but also if the operation of the gambling platform is disrupted, there may be huge losses.
(For example, if there is a wave of attacks on your betting platform during the World Cup, users will not be able to access your betting platform, perform any operations, recharge, or withdraw money. You can imagine how big the loss will be)
However direct financial losses are not the only consequence of cyberattacks. The personal data of your betting platform players may also be compromised. When they gain access to a player's personal account, they can use the information to hack into their email or social media accounts. They may then use the data for ransom or sell it to other malicious actors.
In the gambling industry, such cyber-attacks are common. This is increasing at a rate of 1,000% per year, resulting in an average loss of £3.1 million for gambling operators. This caused significant financial losses and reputational damage to the gambling company. For example, as recently as September 2023, MGM suffered a large-scale cyber attack, forcing it to shut down certain systems across the United States. The incident caused approximately $100 million in damage and took approximately a month to resume normal operations. So this is exactly why bookmakers must take cyber attacks seriously. Especially gambling operators whose main business is iGaming platforms.
Where do cybersecurity threats come from?
The vast world of the Internet is filled with all kinds of people, and their online presence is not necessarily personal or specific to a website or network. These people, whom we usually call hackers, frequently scan the entire Internet looking for vulnerabilities and opportunities that they can exploit. Their goals are extremely broad and there is no specific target. As long as it is within their sight, they may target it.
Among them, some industries have become the focus of hackers due to their special nature. For example, in the highly competitive iGaming industry, competition among peers is not uncommon. In order to win market share and attract more outstanding players, some platforms may use various means, even to suppress competitors. This situation is more common, especially during some large international events.
But not all hacks cause harm. As awareness of cybersecurity increases, so does the number of ethical hacking attacks, also known as white hat hacking. These freelance experts, sometimes called bounty hunters, work to find bugs and vulnerabilities in software or websites and report them to companies in exchange for rewards. Their goal is completely different from that of criminal black hat hackers. Their goal is to help companies fix these vulnerabilities before they are exploited. The lines between these two categories can sometimes become blurred. Some bounty hunters expect to be rewarded for discovering and reporting vulnerabilities, but if they do not receive the rewards they deserve, they may use their knowledge of security vulnerabilities to launch attacks themselves. This makes the network security situation more complex and requires more vigilance and prevention on our part.
Whether you are fighting against attacks by black hat hackers or using the help of white hat hackers to fix vulnerabilities, you need sufficient knowledge and technology as well as resources. In this challenging online world, you want to keep the iGaming iGaming platform stable and safe. If you don't have a major. A strong team maintains your gambling platform, and your gambling platform is always fully exposed to the eyes of your competitors. Attacks on your website can be launched anytime and anywhere.
What are the common cyber-attacks?
1. Port scanning attack
Port scanning refers to someone with ulterior motives sending a set of port-scanning messages in an attempt to invade a computer and learn the type of computer network services it provides (these network services are all related to port numbers). Port scanning is a method favored by computer decryption experts.
Hackers are constantly scanning for weaknesses. This process can be fully automated, including trying to connect to random IP addresses, finding open ports, or guessing passwords. Port scanning is often the start of a cyberattack and is a way for hackers to find vulnerabilities and gain access to your system.
To better understand what a port scan attack is, imagine your server as a cabin in the woods. A hacker is a thief who is constantly circling the door, trying every doorknob, checking under every doormat for a spare key. Or they try to climb in through the window.
Port attackers can use it to learn where to explore attack weaknesses. Essentially, port scanning involves sending messages to each port, one message at a time. The type of response received indicates whether the port is in use and can be used to detect vulnerabilities.
1-2. Which ports are frequently attacked?
When you start your web server for the first time, many services start automatically with open ports and default passwords, leaving you vulnerable to attacks. If a hacker happens to find your IP address during a scan, they can quickly access your data and even gain root (the highest level of privileges) access.
Commonly used ports by attackers include 8080, 21, 22, 23, 25, 80, 102, 110, 111, 119, 135, 161, 177 and 399.
1-3 What are the port scanning methods?
TCP connect scan
TCP scanning is the most basic scanning. The connect system call provided by the operating system is used to connect to the port of each target computer of interest. If the port is in the listening state, the connection will succeed. Otherwise, this port is unavailable, that is, no service is provided.
The biggest advantages of TCP connect scanning are:
No permissions are required: any user on the system has the right to use this call.
Another benefit is speed: by opening multiple sockets simultaneously, scanning is accelerated. Using non-blocking I/O allows you to set a low timeout period and observe multiple sockets simultaneously.
Disadvantages of TCP connect scanning: it is easily detected and filtered out.
TCP SYN scan
TCP SYN scans are often considered "semi-open" scans because the scanner does not have to open a full TCP connection. The scanner sends a SYN packet as if it is preparing to open an actual connection and is waiting for a response.
Advantages of TCP SYN scanning: Generally, no records are left on the target server or computer.
Disadvantages of TCP SYN scanning: You must have root privileges to create your own SYN packet.
TCP FIN scan
Sometimes it is possible that the SYN scan is not secretive enough. Some firewalls and packet filters monitor designated ports, and some programs can detect these scans. But the FIN packet will probably get through without any trouble. Another benefit is that open ports ignore replies to FIN packets.
However, the shortcomings of this method have a certain relationship with the implementation of the system. Some systems reply to RST regardless of whether the port is open, so this scanning method is not suitable.
IP segment scanning
IP segment scanning does not directly send TCP detection packets but divides the data packets into two smaller IP segments. This splits a TCP header into several packets, making it difficult for firewall rule filters to detect it.
TCP reverse ident scan
The ident protocol allows (rfc1413) to see the username of the owner of any process connected over TCP, even if the connection was not initiated by this process. So you can, for example, connect to the http port and then use identd to discover whether the server is running with root privileges. This method can only be seen after a complete TCP connection has been established with the target port.
FTP return attack
FTP return attack The intruder can connect from his own computer to the FTP server-PI (Protocol Interpreter) of the target host to establish a control communication connection. Then, request this server PI to activate a valid server-DTP (data transfer process) to send files to anywhere on your server. (Files can be uploaded, and the consequences are imaginable) The advantages of FTP return attacks are obvious. They are difficult to track and can pass through firewalls. The main disadvantage is that it is very slow.
SEO in the gambling industry generally talks about common attack terms such as site taking, penetration, etc. Many of them are direct port attacks. For example, there was a time when SEOs used to scan a large number of corporate websites, modify files after intrusion, and put in backdoors. Thereby directing normal users to visit their own site. Some people may ask, how much traffic can a corporate website have? But if you just imagine, what if you have hundreds or thousands of corporate websites? It is also very impressive to guide these many small traffic sites to one site. At the same time, having hundreds or thousands of external officials guide them to the target site can also be a positive SEO method. It was also one of the ways to get up quickly.
2. DDoS attack
A DDoS attack is a simple, widespread, direct network security attack that is very crude. DDoS attacks take the form of large amounts of traffic and are designed to overload the target server's core, thereby significantly blocking the communication between the server and the network. At the same time, a large amount of your server resources are consumed, causing the server to crash. Users cannot operate on your gambling platform, and the gambling platform is stuck. Even websites with traffic developed by the SEO personnel under the gambling platform will be subject to this type of attack.
DDoS attacks are very common nowadays. Just pay them. There are companies or teams that specialize in such attacks. Just open a username and recharge. This type of attack is very direct. For example, when a large-scale event comes, if there are so many waves on your betting platform, how many users will your betting platform lose?
The solution is also very simple, it is also a matter of money. Decentralize and manage a large number of your gambling platform network and server resources. This requires large traffic bandwidth support, a large number of IPs, and multiple servers to disperse the attack. In a word, don't let it attack in one place, and use more resources to disperse it so that the attack can withstand the intensity, so as to ensure the stable operation of your gambling platform server. But it may also be said that firewall rules can be used. However, the server itself consumes server resources to determine the rules. Some people will say CDN, but CDN also requires its own funds and technical support. The price of the Internet lines of the gambling platform is not comparable to the price of ordinary Internet lines. Peak traffic is then mitigated through load balancers and scalable resources, while a Web Application Firewall (WAF) is deployed to prevent DDoS attacks. So no matter which method you use to avoid DDoS attacks, you need to have strong resources ready through your own gambling platform server, as well as a quick response operation and maintenance team.
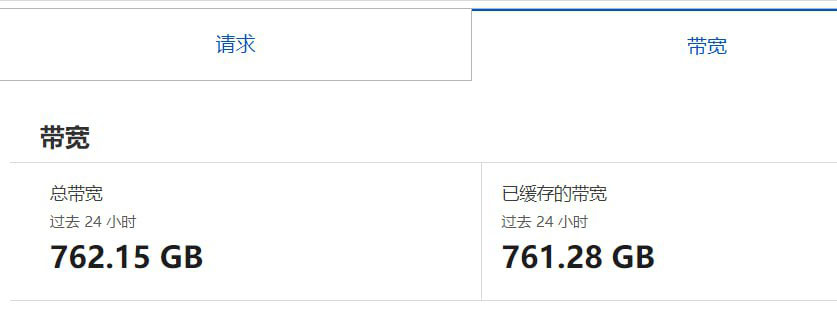
(Like this, it can kill the bandwidth of your server in a few hours, and then your server IP will go into a black hole, and it will be unblocked after a few hours or a few days.)
3. CC attack
CC = Challenge Collapsar, meaning "Challenge Black Hole", its predecessor was called Fatboy Attack, which uses continuous connection requests to the website to cause a denial of service. This is because, in the early stages of the development of DDOS attacks, most of them could be protected by the industry's well-known "black hole" (Collapsar) anti-denial-of-service attack system. Therefore, after hackers developed a new type of DDOS attack targeting HTTP, it was named Challenge Collapsar
Compared with other DDoS attacks, CC seems to be more technical. You won't see fake IPs or particularly large abnormal traffic in this kind of attack, but it will cause the server to be unable to connect normally. An ordinary ADSL user is enough to bring down a high-performance server. But what is even more troublesome is that the technical content of this attack is low. A user with a beginner or intermediate computer level can carry out the attack by using the IP proxy replacement tool and some IP proxies.
CC attacks are targeted at domain names. For example, if the gambling domain name is "www.abc.com", then the attacker will set the attack target to this domain name in the attack tool and then carry out the attack. However after the domain name is unbound, the attack loses its target. The advantage is that the gambling platform will have many backup domain names that can be switched. But if such an attack comes to you at a critical moment, it will also cause heavy losses to the gambling platform. At the same time, if there are no dedicated technicians, they will keep an eye on it 24 hours a day. The loss would be even greater.
Of course, there are many other solutions, such as changing the Web port, blocking IP, domain name spoofing and resolution, setting up a CDN, etc., but in the final analysis, a highly skilled team and resources are still needed to defend against these.
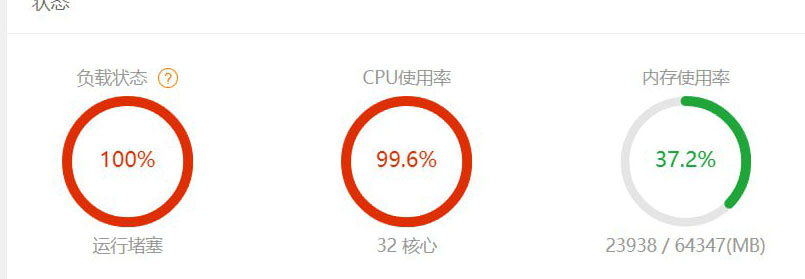
(In this state, you are being attacked by CC. Your server will be stuck in just a few minutes or less than a minute.)
4. SQL injection attack
SQL is a computer language used for database management. Any website driven by a database (most websites) is vulnerable to SQL injection attacks. SQL queries are requests to perform certain operations on the database. Carefully constructed malicious requests can create, modify, or delete data stored in the database, as well as read and extract intellectual property, personal information, and other data. Customer, administrative credentials, or private business details.
SQL attacks use SQL queries sent from the client to the database on the server. The command is inserted or "injected" into the data in place of something else that would normally be there, such as a password or login. The server holding the database then runs the command and the system is compromised.
If SQL injection is successful, several things may happen, including the release of sensitive data or the modification or deletion of important data. Additionally, an attacker could perform administrator actions such as a shutdown command, which could disrupt the functionality of the database.
(After injection, it can create, modify, or delete data stored in the database in your bookmaker or website, as well as read and extract data such as intellectual property, and personal information. Customers, administrative credentials private business details, etc. These are common operations)
Although most of the latest versions of databases are now resistant to the extremely common SQL injection attack. What's more, a large number of gambling packages still use early versions of SQL. Early versions are more vulnerable to SQ, although most of the latest version databases can now resist the extremely common SQL injection attacks. What's more, a large number of gambling packages still use early versions of SQL, and early versions are more vulnerable to SQL injection attacks. Therefore, for many gambling platforms, the database and website are separated and not in the same server unit. A separate safe house is established for the database. At the same time, make database mirror backups from time to time. At that time, many subdivisions were also made in database permission management. Use the least privilege model. Use a least privilege architecture to only allow those who absolutely need access to critical databases. Even if the user has power or influence within the organization. L injection attack. Therefore, for many gambling platforms, the database and website are separated and not in the same server unit. A separate safe house is established for the database. At the same time, make database mirror backups from time to time. At that time, many subdivisions were also made in database permission management. Use the least privilege model. Use a least privilege architecture to only allow those who absolutely need access to critical databases. Even if the user has power or influence within the organization.
5. 5. MITM attack
A man-in-the-middle (MITM) type of cyber attack refers to a network security vulnerability that makes it possible for an attacker to eavesdrop on data sent back and forth between two people, networks, or computers. It's called a "man-in-the-middle" attack because the attacker positions themselves "in the middle" or between the two parties trying to communicate. In effect, the attacker is monitoring the interaction between the two parties. You can also intercept calls between communicating parties and insert new content.
To put it bluntly, the two parties feel as if they are communicating normally. But unbeknownst to each other, the person who actually sent the message illegally modified or accessed the message before it reached its destination. For example: The gambling finance manager wants to communicate with a supervisor or boss. At the same time, the middleman hopes to intercept the stolen conversation in order to eavesdrop and possibly transmit a false message to the supervisor or boss at some point.
Some ways to protect you and your betting team from MITM attacks are to use strong encryption on access points or use a Virtual Private Network (VPN). However, building these dedicated VPNs also requires technology and resources. It is not very reliable to find a VPN on the Internet. No one knows whether the other party is a human or a ghost.
6. Phishing attacks
Phishing attacks occur when a malicious actor sends an email that appears to be from a trusted, legitimate source in an attempt to obtain sensitive information from a target. Phishing attacks combine social engineering and technology and are so named because the attacker is actually "fishing" into restricted areas using a "bait" that appears to be a trustworthy sender.
To carry out an attack, an attacker might send you a link that takes you to a website and then trick you into downloading malware, such as a virus, or providing the attacker with your private information. In many cases, targets may not realize they have been compromised, allowing attackers to track down others in the same organization without anyone suspecting malicious activity.
I think everyone is familiar with this type of attack, and it often occurs in companies or people around them. The editor of Tiancheng Bao.com will not explain too much here.
7.Bait attack
Phishing attacks are called "whales" because their main targets are those who hold important positions in an organization or team and are considered "big fish" or "whales." These individuals may hold information that is valuable to an attacker, or they may have access to channels that are valuable to an attacker. For example, these people might be the head of the revenue department of a bookmaker, or they might be people or managers in a key department that specializes in running a company.
If these whales are targeted and they download or inadvertently install ransomware, there is a good chance they will choose to pay the ransom to avoid the successful cyberattack becoming public and causing harm to themselves or their organization. damage. Therefore, the main way to deal with whale phishing attacks is to carefully check all emails and links or files on social media, and be alert to anything that looks suspicious.
Therefore, a reliable and safe office environment is necessary.
8.Spear Phishing Attacks
Spear phishing is a highly specialized and targeted form of cyberattack. In this type of attack, attackers spend a lot of time researching their intended target in order to obtain large amounts of personal information. They would then use this information to craft an email or message that seemed closely related to the target's personal life. What’s unique about this approach is that the attacker specializes their attack on a specific target, making the message and source look very legitimate, which is why spear phishing attacks are so difficult to detect.
In spear phishing attacks, attackers typically use techniques similar to those used in regular phishing attacks. For example, they may forge the "sender" information of an email to make it appear that the email is from someone the target knows. This "acquaintance" may be the target's friends, family, business associates, or contacts in a social network. In addition, attackers may also use website cloning to copy the interface and content of a legitimate website, allowing targets to lower their guard when entering their private information.
But iGaming operators, beware; this type of attack is usually not carried out alone but is combined with other attack methods to increase the effectiveness of the threat. For example, on the betting platform, attackers may use CC attacks or other methods to make the main website unable to be opened. Then, at this time, they will use man-in-the-middle attacks or other means to inform customers of the URL of the betting platform, such as telling them The URL of their website has been moved to a new URL, requiring customers to re-register. This type of operation is not uncommon in the iGaming industry and has caused losses to many users.
9.Ransomware
The use of ransomware is a despicable form of cyber attack in which the victim's operating system is held hostage by malicious attackers unless they are willing to pay a ransom to these attackers. Typically, only after the victim pays the ransom will the attacker provide an unlocking password or related steps to help the victim regain control of their computer.
During this type of ransomware attack, victims usually accidentally download a file or link containing malware while browsing a website or opening an email attachment. This malware usually operates by exploiting unsolved vulnerabilities in the operating system or IT firmware, or security vulnerabilities that have not yet been discovered. Sometimes ransomware takes the form of a coordinated attack, unknowingly taking over an entire network environment by denying access to multiple computers or attacking central servers critical to business operations.
This malware can be spread in various ways. It can be spread through internal networks or via Universal Serial Bus (USB) drives connected to multiple computers, sending AUTORUN files containing malicious programs from one system to another. system.
During the design process, the authors of this type of ransomware may have faced traditional anti-virus software and network security protection measures as their biggest opponents. Therefore, all users of the Internet, especially those working at gambling offices, need to be extremely vigilant about the sites they visit and the links they click. At the same time, it may be necessary to add a firewall (NGFW) to the network to prevent many ransomware attacks and ensure the security and stability of the network.
10.Password attack
Passwords are a common access verification tool that attracts hackers to crack. Methods include: finding paper copies of passwords, intercepting unencrypted network transmissions, using social engineering to convince targets to enter passwords, or guessing default or simple passwords.
Hackers also use brute force to guess passwords based on personal or job information, such as name, birthday, etc. Information exposed on social media, such as pet names or hobbies, may also be used to guess passwords. Dictionary attacks, in which passwords are guessed using common words and phrases, are also a hacker's tactic.
An effective way to prevent brute force and dictionary attacks is to set up a lockout policy that automatically locks access after multiple failed attempts. If the account is locked, it is recommended to change the password. If a hacker guesses a password using brute force or a dictionary attack, they may make a note of the invalid password so they can try it next time.
URL guessing/explanation
URL paraphrasing is a cyberattack method by which an attacker can change and forge specific URL addresses and use them to access a target's personal and professional data. This attack is also known as URL poisoning. The term "URL interpretation" comes from the fact that an attacker understands and exploits the sequence of URL information in a web page to carry out an attack.
When performing a URL interpretation attack, a hacker may try to guess the URL that could gain site administrator rights or gain access to the site's backend to break into a user's account. Once they find and get to the page they want, they can manipulate the site itself, or access sensitive information about people using the site.
For example, if a hacker were trying to get into the admin section of a website called http://abc.com, they might enter http://abc.com/admin, which would take them to the admin login page. In some cases, the administrator username and password may be the default "admin" and "admin" or be easily guessed. The attacker may also have figured out the administrator's password or narrowed it down to a few possibilities. The attacker then tries each one, and once they gain access, they can manipulate, steal, or delete the data at will.
To prevent URL interpretation attacks from being successful, you need to use secure authentication for any sensitive areas of your site. Regularly updating and strengthening the security protection measures of the website can only be a daily precaution. The most important thing is to use the latest security protocols and encryption technologies. This ensures that even if an attacker attempts a URL interpretation attack, they cannot easily obtain sensitive information.
12.DNS spoofing and hijacking DNS spoofing
DNS spoofing
DNS spoofing is a typical network attack method in which hackers invade a personal computer and then change local DNS records to redirect network traffic to fake or so-called "spoofed" websites. When users try to access the websites they use every day, they are actually redirected to the website the attacker wants them to see. For example, if you try to access an iGaming platform, such as ao.com, you may be redirected to a similar but slightly different URL, such as a0.com. The attacker-controlled website may provide some explanations or guide users to take certain actions. In this case, the loss of the gambling website ao.com not only includes its gamblers, but more importantly, its brand reputation and customer trust, which cannot be measured in terms of money.
DNS hijacking
DNS hijacking is usually a more large-scale attack, usually involving gambling website operators teaming up to carry out large-scale hijacking, which may affect an entire region. For example, assuming that an authorized employee of the China Unicom operator in Jiangxi carries out DNS hijacking for the domain name A.COM, then all users of China Unicom A.COM in Jiangxi will be redirected to the attacker when they open the web page. designated website. After discovering this kind of attack, although you can try to clean the domain name DNS, the effect may not completely solve the problem. This kind of hijacking was very common among gambling websites in the past because it was a common method used by them to compete with their competitors.
13. Cross-site scripting
Cross-site scripting (XSS) is a special type of web injection attack in which a cyber attacker injects data, such as malicious script, into content from another trusted website. This can happen when an untrusted source is allowed to inject its own code into a web application and the malicious code is included in the dynamic content delivered to the victim's browser. This gives cyber attackers the ability to execute malicious scripts written in a variety of languages, including but not limited to JavaScript, Java, Ajax, Flash, and HTML, in another user's browser.
Cross-site scripting (XSS) attacks allow attackers to steal session cookies, allowing attackers to impersonate users. Furthermore, it can be used to spread malware, disrupt the normal functioning of websites, or cause havoc on social networks. Attackers can also use cross-site scripting (XSS) for phishing to obtain users' credentials, or even combine it with social engineering techniques to carry out more destructive attacks. Cross-site scripting (XSS) is an attack method often used by hackers. In the 2022 CWE Top 25, it is listed as the second most common attack method, highlighting its importance in the field of network security.
How to prevent losses on your iGaming platform?
Keep software up to date
Software is a very complex thing, and cunning hackers are always looking for its weaknesses. Although developers will fix bugs and plug loopholes to protect the system, it is really important to actually implement these changes and maintain security protection.
Remember the famous WannaCry hacking incident in May 2017? That incident caused companies in 150 countries to lose US$4 billion. All this can be prevented by simply downloading a neglected update.
Similar things can happen to iGaming platforms that don’t pay enough attention to network security. If hackers find out-of-date parts of your system, they can exploit vulnerabilities that developers fix in subsequent versions.
However, if a white label iGaming company with experience and a proven track record provides services for your gambling platform from the beginning, it is generally unlikely to become a target of attacks. The reason is that its cost, time, and difficulty have all greatly increased. It is cheap and easy for attackers to attack less secure systems. This is the result they want.
Make sure employees are trained
Even the most stealthy and elaborate hacking attacks, generally regardless of their sophistication, cannot do without human involvement. This involvement could be clicking on a tempting but fraudulent link, downloading a file that is unverified or of unknown security, or unintentionally pressing a potentially dangerous button. This is because the success of a hacker attack often relies on these seemingly insignificant actions, and it is these actions that allow hackers to achieve their destructive goals.
Therefore, if a company's employees can learn how to identify and respond to cybersecurity threats through professional training, they can become an impenetrable defense barrier. In this way, they not only effectively defend against all forms of cyberattacks, but also protect the company's cybersecurity from any threats that could cause damage to the company.
At the same time, the network layout of the gambling platform also needs to be handled by professional IT personnel with highly skilled skills. This way, they can leverage their expertise and experience to minimize the likelihood of a cyberattack occurring from within. This strategy of strengthening defense both internally and externally is an important means to ensure company network security.
Summary
The editor of TC-Gaming today mainly discussed the network security issues of iGaming platforms. Whether you are a small business or a large bookmaker, you can be subject to a cyber attack. In addition, cyberattacks will not only cause direct economic losses but may also lead to the personal data of gambling platform players being violated. Therefore, strict maintenance and management of network security is necessary.
In the highly competitive iGaming industry, competition among peers leads to more security threats. After a gambling company has completed its internal office network, it also needs to pay attention to other types of network attacks, such as CC attacks, SQL injections, DDoS attacks, etc. These attack methods require a skilled network team to conduct 24-hour server monitoring and troubleshooting. In the event that there is an issue with your iGaming platform, they should be able to respond quickly and resolve the issue.
Cyber attacks come in many forms are complex, and are usually not limited to a single attack method. Therefore, rapid judgment and response to attacks and solving attack problems require rich experience and professional knowledge. This is why when choosing a package network company, everyone tends to choose a company with strength and reputation.
For example, in order to save costs, some teams or small groups may choose to obtain a package network system from elsewhere and put it into use after slight modifications. However, the system they took from somewhere else may have a backdoor that the other party may not even know about. Or, the team themselves might leave a backdoor in the system. This highlights the importance of choosing a white label iGaming company or team.
The stable operation of iGaming platforms is crucial. No matter how great your marketing strategy is, if there is a problem with your white label iGaming system, all your efforts may be in vain and serve as a wedding dress for your competitors. Therefore, in terms of network security, we need to maintain a high degree of vigilance and attention and choose a powerful and reputable Internet company to ensure the stable operation of the gambling platform.
With its excellent reputation, wide popularity, and rich experience in the gaming market, TC-Gaming has in-depth insights into and accurately analyzes the iGaming market. As a package network company with a long history, we have accumulated more than 16 years of white label iGaming experience. With a skilled R&D team and an enthusiastic and dedicated pre-sales and after-sales team, TC-Gaming White Label iGaming focuses on providing white label iGaming platform and API game interface services for the global gambling market and is equipped with an all-weather service team. In addition to our outstanding performance in software and hardware technology, we are even more proud of the excellent market trust and reputation we have built over the past 16 years. We always live up to the trust of our customers, constantly innovate to meet the needs of customers and players, and are committed to developing diversified entertainment services. Choose TC-Gaming and you will surely achieve success.
Due to the frequent incidents of white label fraud, please contact us through the following official social media accounts




